| Oracle® Database Vault Administrator's Guide 11g Release 1 (11.1) Part Number B31222-01 |
|
|
View PDF |
| Oracle® Database Vault Administrator's Guide 11g Release 1 (11.1) Part Number B31222-01 |
|
|
View PDF |
The Oracle Database Vault objects include two schemas with database tables, sequences, views, triggers, roles, packages, procedures, functions, and contexts that support the administration and run-time processing of Oracle Database Vault.
This chapter includes the following sections:
Oracle Database Vault has the following schemas:
DVSYS Schema: Owns the Oracle Database Vault schema and related objects
DVF Schema: Owns the Oracle Database Vault functions that are created to retrieve factor identities
The DVSYS schema contains Oracle Database Vault database objects, which store Oracle Database Vault configuration information and support the administration and run-time processing of Oracle Database Vault.
Oracle Database Vault secures the DVSYS schema by using a protected schema design. A protected schema design guards the schema against improper use of system privileges (for example, SELECT ANY TABLE, CREATE ANY VIEW, or DROP ANY).
Oracle Database Vault protects and secures the DVSYS schema in the following ways:
The DVSYS protected schema and its administrative roles cannot be dropped. By default, the DVSYS account is locked.
Statements such as CREATE USER, ALTER USER, DROP USER, CREATE PROFILE, ALTER PROFILE, and DROP PROFILE can only be issued by a user with the DV_ACCTMGR role. SYSDBA can issue these statements only if it is allowed to do so by modifying the Can Maintain Accounts/Profiles rule set.
The powerful ANY system privileges for database definition language (DDL) and data manipulation language (DML) commands are blocked in the protected schema. This means that the objects in the DVSYS schema must be created by the schema account itself. Also, access to the schema objects must be authorized through object privilege grants.
Object privileges in the DVSYS schema can only be granted to administrative roles in the schema. This means that users can access the protected schema only through predefined administrative roles.
Only the protected schema account DVSYS can issue ALTER ROLE statements on predefined administrative roles of the schema. "Oracle Database Vault Roles" describes Oracle Database Vault administrative roles in detail.
Only the protected schema account DVSYS can grant predefined roles to users along with the ADMIN OPTION. This means that a grantee with the ADMIN OPTION can grant the role to another user without the ADMIN OPTION.
The SYS.DBMS_SYS_SQL.PARSE_AS_USER procedure cannot be used to run SQL statements on behalf of the protected schema DVSYS.
Note:
Database users can grant additional object privileges and roles to the Oracle Database Vault Administrative roles (DV_ADMIN and DV_OWNER, for example) provided they have sufficient privileges to do so.The DVF schema is the owner of the Oracle Database Vault DBMS_MACSEC_FUNCTION PL/SQL package, which contains the functions that retrieve factor identities. After you install Oracle Database Vault, the installation process locks the DVF account to better secure it. When you create a new factor, Oracle Database Vault creates a new retrieval function for the factor and saves it in this schema.
This section describes the default roles Oracle Database Vault provides. It includes the following topics:
Oracle Database Vault Application Resource Owner Role, DV_REALM_RESOURCE
Oracle Database Vault Configuration Administrator Role, DV_ADMIN
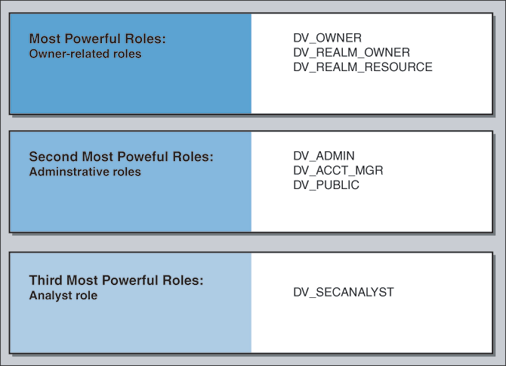
Oracle Database Vault provides a set of roles that are required for managing Oracle Database Vault. These roles are designed to implement the first level of separation of duties within the database, organized in the following hierarchy: The most powerful level is for the owner-related roles, DV_OWNER, DV_REALM_OWNER, and DV_REALM_RESOURCE. The next level beneath it is for the administrative roles, DV_ADMIN, DV_ACCTMGR, and DV_PUBLIC. The third level is for the analyst-related role, DV_SECANALYST.
Figure D-1 illustrates the hierarchy of Oracle Database Vault roles, based on their levels of power.
Figure D-1 Hierarchy of Oracle Database Vault Roles
Note:
You can grant additional object privileges and roles to the Oracle Database Vault roles to extend their scope of privileges. For example,SYSDBA can grant object privileges to an Oracle Database Vault role as long as the object is not in the DVSYS schema or realm.Table D-1 summarizes the privileges available with Oracle Database Vault roles.
Table D-1 Privileges of Oracle Database Vault Roles
| Privilege | DV_OWNER | DV_REALM_OWNER | DV_REALM_RESOURCE | DV_ADMIN | DV_ACCTMGR | DV_SECANALYST | DV_PUBLIC |
|---|---|---|---|---|---|---|---|
|
|
Yes |
No |
No |
Yes |
No |
No |
No |
|
|
Yes |
No |
No |
Yes |
No |
No |
No |
|
|
Yes |
No |
No |
No |
No |
YesFoot 1 |
YesFoot 2 |
|
|
No |
No |
No |
No |
No |
No |
Yes |
|
|
Yes |
No |
No |
No |
No |
No |
No |
|
|
No |
No |
No |
No |
No |
Yes |
No |
|
Monitor Database Vault |
Yes |
No |
No |
Yes |
No |
Yes |
Yes |
|
Run Database Vault reports |
Yes |
No |
No |
Yes |
No |
Yes |
Yes |
|
|
Yes |
No |
No |
No |
No |
Yes, on some system views |
No |
|
|
No |
No |
No |
No |
No |
Yes, portions of |
No |
|
|
No |
No |
No |
No |
Yes |
No |
No |
|
Manage objects in schemas that define a realmFoot 4 |
No |
Yes |
No |
No |
No |
No |
No |
|
|
No |
No |
Yes |
No |
No |
No |
No |
|
|
No |
No |
Yes |
No |
No |
No |
No |
|
|
No |
No |
Yes |
No |
No |
No |
No |
Footnote 1 DV_SECANALYST can query DVSYS schema objects through Oracle Database Vault-supplied views only.
Footnote 2 DV_PUBLIC can query DVSYS schema objects through Oracle Database Vault-supplied views only.
Footnote 3 This privilege does not include the ability to drop or alter the DVSYS account, nor change the DVSYS password.
Footnote 4 This privilege includes ANY privileges, such as CREATE ANY, ALTER ANY, and DROP ANY.
Footnote 5 The RESOURCE role provides the following system privileges: CREATE CLUSTER, CREATE INDEXTYPE, CREATE OPERATOR, CREATE PROCEDURE, CREATE SEQUENCE, CREATE TABLE, CREATE TRIGGER, CREATE TYPE.
Use the DV_OWNER role manage the Oracle Database Vault roles and its configuration. The DV_OWNER role has the administrative capabilities that the DV_ADMIN role provides, and the reporting capabilities the DV_SECANALYST role provides. It also provides privileges for monitoring Oracle Database Vault. It is created when you install Oracle Database Vault, and has the most privileges on the DVSYS schema. (In this guide, the example account that uses this role is MACSYS.) In addition to DV_ADMIN role, the DV_OWNER role has the GRANT ANY ROLE, ADMINISTER DATABASE TRIGGER, ALTER ANY TRIGGER privileges, and EXECUTE privileges on the SYS.DBMS_RLS package.
The first account, which is typically the account created during the installation as the Database Vault Owner, granted with this role and the ADMIN OPTION can grant any Oracle Database Vault roles (except DV_ACCTMGR) without the ADMIN OPTION to any account. Users granted this role also can run Oracle Database Vault reports and monitor Oracle Database Vault.
Anyone with the DV_OWNER role or privilege can grant the DV_OWNER role to another user. The account granted this role and with the ADMIN OPTION can revoke any granted protected schema role from another account. Accounts such as SYS or SYSTEM, with the GRANT ANY ROLE system privilege alone (directly granted or indirectly granted using a role) do not have the rights to grant or revoke the DV_OWNER role from any other database account.
The granting and revoking of all protected schema roles, including DV_OWNER, are enforced only by an instance with the Oracle executable linked with DV_ON, which enables Oracle Database Vault security. When the Oracle executable is linked with DV_OFF, then an instance can use an account GRANT ANY ROLE system privilege for GRANT and REVOKE operations.
Appendix B, "Enabling and Disabling Oracle Database Vault" shows how to use DV_ON and DV_OFF.
Use the DV_REALM_OWNER role to manage database objects in multiple schemas that define a realm. This role should be granted to the database account owner who would manage one or more schema database accounts within a realm and the roles associated with the realm. A user granted this role can use powerful system privileges like CREATE ANY, ALTER ANY, and DROP ANY within the realm.
The realm owner of the Oracle Data Dictionary realm, such as SYS, can grant this role to any given database account or role. Note that though this role has system privilege grants that SYS controls, it does not have the DV_OWNER or DV_ADMIN roles.
If you want to attach this role to a specific realm, you need to assign it to an account or business-related role, then authorize that account or role in the realm.
The DV_REALM_RESOURCE role provides the same system privileges as the Oracle RESOURCE role. In addition, both CREATE SYNONYM and CREATE VIEW are granted to this role.This role can be granted to a database account that will own database tables, objects, triggers, views, procedures, and so on that are used to support any database application. This is a role geared toward a schema type database account. The realm owner of the Oracle Data Dictionary realm, such as SYS, can grant this role to any database account or role. Note that though this role has system privilege grants that SYS controls, it does not have the DV_OWNER or DV_ADMIN privileges.
The DV_ADMIN role has the EXECUTE privilege on the DVSYS packages (DBMS_MACADM, DBMS_MACSECROLES, and DBMS_MACUTL). DV_ADMIN also has the capabilities provided by the DV_SECANALYST role, which allow the user to run Oracle Database Vault reports and monitor Oracle Database Vault.
Accounts such as SYS or SYSTEM, with the GRANT ANY ROLE system privilege alone do not have the rights to grant or revoke DV_ADMIN from any other database account. The first user with the DV_ADMIN role and the ADMIN OPTION can grant this role without the ADMIN OPTION to any database account and revoke this role from another account.
The granting and revoking of protected schema roles, including DV_ADMIN, are enforced only by an instance with the Oracle executable linked with DV_ON, which enables Oracle Database Vault security features. When the Oracle executable is linked with DV_OFF, then an instance can use an account GRANT ANY ROLE system privilege for GRANT and REVOKE operations.
Appendix B, "Enabling and Disabling Oracle Database Vault" explains how to use DV_ON.
Use the DV_ACCTMGR role to create and maintain database accounts and database profiles. A user who has been granted this role can use the CREATE, ALTER, and DROP statements for users or profiles. However, a person with this role cannot use the DROP or ALTER statements for the DVSYS account, nor change the DVSYS password.
Tip:
Oracle recommends that you add the user who has theDV_ACCTMGR role to the data dictionary realm so that this user can grant other users ANY privileges, if they need them. See "Step 1: Adding the SYSTEM User to the Data Dictionary Realm" for instructions.Any account, such as SYS or SYSTEM, with the GRANT ANY ROLE system privilege alone does not have the rights to grant this role to or revoke this role from any other database account. The first account with the DV_ACCTMGR role and the ADMIN OPTION can grant this role without the ADMIN OPTION to any given database account and revoke this role from another account.
The granting and revoking of protected schema roles are enforced only by an instance with the Oracle executable linked with DV_ON, which enables Oracle Database Vault. When the Oracle executable is linked with DV_OFF, then an instance can use an account with GRANT ANY ROLE system privilege for GRANT and REVOKE operations.
Appendix B, "Enabling and Disabling Oracle Database Vault" shows how to use DV_ON and DV_OFF.
Use the DV_PUBLIC role to grant privileges on specific objects in the DVSYS schema. Oracle Database Vault does not enable you to directly grant object privileges in the DVSYS schema to PUBLIC. You must grant an the object privilege on the DVSYS schema object the DV_PUBLIC role, and then grant DV_PUBLIC to PUBLIC. However, if you do this, it is important that you do not add more object privileges to the PUBLIC role. Doing so may undermine Oracle Database Vault security.
The following Oracle Database Vault objects are accessible through DV_PUBLIC:
PL/SQL procedures and functions, described in "Oracle Database Vault Run-Time PL/SQL Procedures and Functions". These enable access control and Oracle Label Security processing in an Oracle database.
PL/SQL factor functions, described in "Oracle Database Vault PL/SQL Factor Functions". For the DVF schema, these are functions for each factor defined. These are functions that you can use in rule sets to inspect the SQL statement that you want the rule set to protect.
DVSYS.DBMS_MACSEC_ROLES package, described in Appendix F, "Oracle Database Vault DVSYS.DBMS_MACSEC_ROLES Package". This package enables you to check the authorization for a user or to set an Oracle Database Vault secure application role.
DVSYS.DBMS_MACUTL package, described in Appendix G, "Oracle Database Vault DVSYS.DBMS_MACUTL Package". This package is a set of general purpose utility functions that you can use throughout the application code you write for Oracle Database Vault.
Use the DV_SECANALYST role to run Oracle Database Vault reports and monitor Oracle Database Vault. (This role is also used for database-related reports.) In addition, this role enables you to check the DVSYS configuration by querying the DVSYS views described in "Oracle Database Vault Public Views". The DV_SECANALYST role has SELECT privileges on the DVSYS schema objects and portions of the SYS and SYSMAN schema objects for reporting on DVSYS- and DVF-related entities.
Any account, such as SYS or SYSTEM, with the GRANT ANY ROLE system privilege alone does not have the rights to grant this role to or revoke this role from any other database account. The user with the DV_SECANALYST role and the ADMIN OPTION can grant this role without the ADMIN OPTION to any database account and revoke this role from another account.
The granting and revoking of protected schema roles are enforced only by an instance with the Oracle executable linked with DV_ON, which enables the Oracle Database Vault security features. When the Oracle executable is linked with DV_OFF, then an instance can use an account GRANT ANY ROLE system privilege for GRANT and REVOKE operations.
Appendix B, "Enabling and Disabling Oracle Database Vault" shows how to use DV_ON and DV_OFF.
Oracle Database Vault prompts for two accounts during installation: Oracle Database Vault Owner and Oracle Database Vault Account Manager. You must supply an account name and password for the Oracle Database Vault Owner account during installation. Creating an Oracle Database Vault Account Manager is optional.
The Oracle Database Vault Owner account is granted the DV_OWNER role. This account can manage Oracle Database Vault roles and configuration.
The Oracle Database Vault Account Manager account is granted the DV_ACCTMGR role. This account is used to manage database user accounts to facilitate separation of duties.
If you prefer to use an existing account to act as the Database Vault Owner and Account Manager, you can grant these roles to the account.
Note:
If you opt not to create the Oracle Database Vault Account Manager account during installation, then both theDV_OWNER and DV_ACCTMGR roles are granted to the Oracle Database Vault Owner user account.Table D-2 lists the Oracle Database Vault database accounts that are needed in addition to the accounts that you create during installation.
Table D-2 Database Accounts Used by Oracle Database Vault
| Database Account | Roles and Privileges | Description |
|---|---|---|
|
Several system and object privileges are provided to support Oracle Database Vault. The ability to create a session with this account is revoked at the end of the installation, and the account is locked. |
Owner of Oracle Database Vault schema and related objects |
|
|
A limited set of system privileges are provided to support Oracle Database Vault. The ability to create a session with this account is revoked at the end of the installation, and the account is locked. |
Owner of the Oracle Database Vault functions that are created to retrieve factor identities |
|
|
This account is created when you install Oracle Label Security by using the Oracle Universal Installer custom installation option. (It is not created when you install Oracle Database Vault.) Do not drop or re-create this account. If you plan to integrate a factor with an Oracle Label Security policy, you must assign this user as the owner of the realm that uses this factor. See "Using an Oracle Database Vault Factor with an Oracle Label Security Policy" for more information. |
Owner of the Oracle Label Security schema |
You can create different database accounts to implement the separation of duties requirements for Oracle Database Vault. Table D-3 lists some model database accounts that can act as a guide. (The accounts listed in Table D-3 serve as a guide to implementing Oracle Database Vault roles. These are not actual accounts that are created during installation.)
Table D-3 Model Oracle Database Vault Database Accounts
| Database Account | Roles and Privileges | Description |
|---|---|---|
|
|
|
Account that is the realm owner for the
|
|
|
|
Account for administration of database accounts and profiles. This account can:
Note: This account cannot create roles, or grant the |
|
|
|
Account to serve as the access control administrator. This account can:
Note: This account cannot directly update the |
|
|
|
Account for running Oracle Database Vault reports in the Oracle Database Vault Administration application. |
The general approach to creating database accounts and using the database roles provided in a database protected by Oracle Database Vault is as follows:
Log in as the Oracle Database Vault account manager (that is, using the DV_ACCTMGR role) to create the new database account.
Grant the new account the ability to create a database session.
Depending on the type of account being created, log in as the Oracle Data Dictionary realm owner or Oracle Database Vault realm owner to grant the appropriate roles required for the account.
Grant additional system or object privileges as required by the account.
The following examples demonstrate the uses of the Oracle Database Vault roles and database accounts. The examples assume the creation of an application schema type account named bizapp, a realm-owner type account named mary, an application end-user type account named jiawen, and a security administrator named steve.
These examples assume that you have added the DV_ACCTMGR role to the Data Dictionary realm. See "Step 1: Adding the SYSTEM User to the Data Dictionary Realm" for instructions on how to do this.
Example D-1 Creating a Schema Account
SQL> CONNECT jgodfrey -- connect using the DV_ACCTMGR role Enter password: password SQL> CREATE USER bizapp IDENTIFIED BY password; -- provide session connectivity SQL> GRANT CONNECT TO bizapp;
SQL> CONNECT SYS / AS SYSDBA
Enter password: password
-- provide the ability to create database objects
SQL> GRANT dv_realm_resource TO bizapp;
SQL> GRANT UNLIMITED TABLESPACE TO bizapp;
SQL> CONNECT bizapp
Enter password: password
SQL> CREATE TABLE bizapp.cases...;
Example D-2 Creating an Account for a Realm Owner
SQL> CONNECT jgodfrey -- connect using the DV_ACCTMGR role Enter password: password SQL> CREATE USER mary IDENTIFIED BY password; -- provide session connectivity SQL> GRANT CONNECT TO mary;
SQL> CONNECT ebrown
-- connect using the DV_OWNER role
Enter password: password
-- provide ANY system privileges a realm owner would need
SQL> GRANT dv_realm_owner TO mary;
SQL> CONNECT mary
Enter password: password
SQL> ALTER TABLE bizapp.cases
Example D-3 Creating an Account for an Application User
SQL> CONNECT jgodfrey -- connect using the DV_ACCTMGR role Enter password: password SQL> CREATE USER jiawen IDENTIFIED BY password; SQL> DEFAULT TABLESPACE low_ts TEMPORARY TABLESPACE low_ts; -- provide session connectivity SQL> GRANT CONNECT TO jiawen; -- the realm owner can manage privileges against realm objects SQL> CONNECT mary Enter password: password SQL> GRANT SELECT ON bizapp.cases TO jiawen; SQL> CONNECT jiawen Enter password: password -- query application tables SQL> SELECT * FROM bizapp.cases
Example D-4 Creating an Account for a Security Administrator
SQL> CONNECT jgodfrey -- connect using the DV_ACCTMGR role Enter password: password SQL> CREATE USER steve IDENTIFIED BY password; SQL> DEFAULT TABLESPACE high_ts; -- provide session connectivity SQL> GRANT CONNECT TO steve;
-- allow execute privileges on DBMS_MACADM package -- and the ability to query access control views SQL> GRANT dv_admin TO steve
-- query and administer access control configuration SQL> CONNECT steve -- connect as the system administrator Enter password: password SQL> SELECT * FROM dvsys.dba_dv_factor; SQL> EXEC dvsys.dbms_macadm.create_factor(...);
Oracle Database Vault provides a set of DBA-style views that can be accessed through the DV_SECANALYST role or the DV_ADMIN role. (Alternatively, you can run reports on Oracle Database Vault. See Chapter 11, "Oracle Database Vault Reports" for more information.) These views provide access to the various underlying Oracle Database Vault tables in the DVSYS and LBACSYS schemas without exposing the primary and foreign key columns that may be present. These views are intended for the database user to report on the state of the Oracle Database Vault configuration without having to perform the joins required to get the labels for codes that are stored in the core tables or from the related tables.
Table D-4 describes the Oracle Database Vault public views.
Table D-4 Oracle Database Vault Views