| Oracle® Database Advanced Security Administrator's Guide 10g Release 1 (10.1) Part Number B10772-01 |
|
|
View PDF |
| Oracle® Database Advanced Security Administrator's Guide 10g Release 1 (10.1) Part Number B10772-01 |
|
|
View PDF |
This chapter describes the sequence of steps involved to configure Enterprise User Security from the initial database and directory preparation through connecting to the database as either a password-, Kerberos-, or SSL-authenticated enterprise user. In addition, a troubleshooting section is also included that will help you when testing your Enterprise User Security implementation.
This chapter contains the following topics:
Configuring Enterprise User Security essentially consists of creating shared schemas and global roles in databases that you want to be accessible to enterprise users. Then you configure the identity management realm in the directory to reflect those database roles and schemas, and, finally, associate directory users with them. Regardless of the authentication method you choose--password, SSL, or Kerberos--you must still create the global database objects and configure the identity management realm as described.
The primary difference between configuration for the various authentication types lies with network connection configuration. You must consider the following three connections:
Enterprise User Security supports many combinations of authentication types between databases, directories, and clients. The three most common implementations of Enterprise User Security, which will be described in this chapter, use the following authentication methods for client/database and database/directory connections:
Primarily, your network environment--whether all clients, databases, and directories reside within the same network behind a firewall, or are distributed across several networks and perhaps exposed to the Internet--determines what authentication type you choose for Enterprise User Security network connections. Security and integrity of enterprise data depend on secure network connections.
Secondarily, the configuration complexity, additional software, and ongoing maintenance required by more rigorous authentication types, such as SSL and Kerberos, should also be considered when choosing which "flavor" of Enterprise User Security to use.
Figure 12-1 shows the configuration process for Enterprise User Security. It is a step-by-step process with decision points based on your implementation and how your users are authenticated. Note that the steps which are represented with broken lines are optional steps in the configuration process.
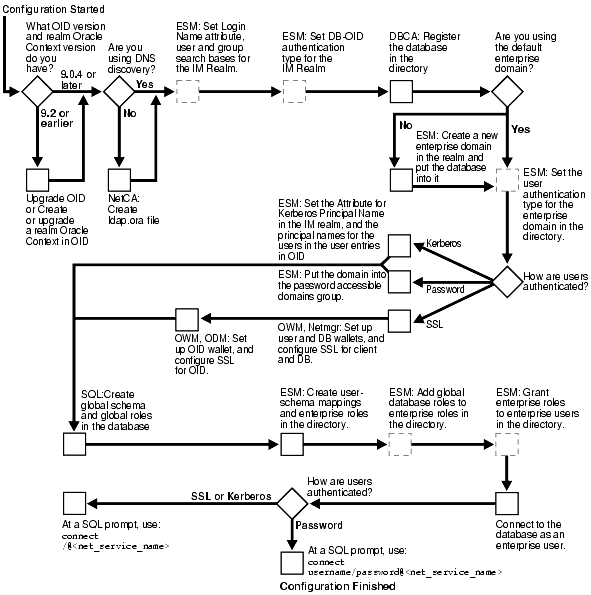
Text description of the illustration asoag034.gif
For brevity, some product names and features have been abbreviated in this flow chart. The following table lists the abbreviations used and their corresponding meaning:
| See Also:
Chapter 11, "Getting Started with Enterprise User Security" for information about the realm Oracle Context, its administrative groups, and entries that pertain to Enterprise User Security. |
The rest of this section provides detailed descriptions of these configuration steps, which should be performed in the following order:
This is the first phase in configuring Enterprise User Security and must be performed before you can configure any other part of this feature.
Enterprise User Security, 10g Release 1 (10.1) requires Oracle Internet Directory, Release 9.0.4, or later, which installs with the required version of the Oracle schema. This schema is backward compatible. After you have installed Oracle Internet Directory, perform the following directory usage configuration tasks:
If necessary, use Oracle Internet Directory Self-Service Console (Delegated Administration Service) to create an identity management realm in the directory. You can also use this tool to upgrade an Oracle9i Oracle Context to a 9.0.4 version Identity Management Realm.
You must have a version 9.0.4 identity management realm to use an Oracle Database 10g. Version 9.0.4 realms are backward compatible to Oracle9i, so you can register Oracle9i and version 10g Oracle Databases in the same realm and place them in the same domain, if desired.
If you do not want to use the default settings, then use Enterprise Security Manager Console to set the user search base, group search base, attribute for login name (nickname attribute), and to set up the necessary context administrators in the identity management realm you plan to use in the directory. To perform this task, see "Setting Properties of an Identity Management Realm".
Identify administrative users in the directory who are authorized to perform the following tasks:
If administrative users do not already exist who can perform these tasks, then see Chapter 13, "Administering Enterprise User Security" to create them.
By default, the identity management realm database-to-directory authentication type is set to passwords. If you do not want to use this default setting, then use Enterprise Security Manager to change it. For example, if you are using a public key infrastructure (PKI), then you would need to set this to SSL. See "Setting the Default Database-to-Directory Authentication Type for an Identity Management Realm".
|
Note:
|
If you use Domain Name System (DNS) discovery (automatic domain name lookup) to locate the directory on your network, then this step is not necessary. (See Oracle Internet Directory Administrator's Guide for information about DNS server discovery.) If you are not using DNS discovery, then you must use Oracle Net Configuration Assistant to create an ldap.ora file for your Oracle home. This configuration file specifies the directory host and port information, and the location of the identity management realm so the database can connect to the directory. (See "Starting Oracle Net Configuration Assistant")
ldap.ora file for your Oracle home.
After you have configured your Oracle home for directory usage, use Database Configuration Assistant to register the database in the directory. Registration creates an entry in the directory so the database can bind, or log in, to it.
When a database is registered in the directory, Database Configuration Assistant performs the following configuration tasks:
LDAP_DIRECTORY_ACCESS parameter in the database initialization parameter file to the default authentication type for the specified identity management realm. This parameter determines whether and how the database attempts authentication to the directory. The allowable settings are NONE, PASSWORD, or SSL. The default setting is PASSWORD.cn=<short_database_name>,cn=OracleContext,<realm_DN> where short_database_name is the first part of the fully qualified domain name for a database. For example, if you have a database named db1.us.oracle.com, then the short database name is db1./admin/Oracle_SID/wallet in UNIX environments and at ORACLE_BASE\ORACLE_HOME\admin\Oracle_SID\wallet in Windows environments. If a database wallet already exists, then Database Configuration Assistant uses it and updates the wallet password.You must be a member of the OracleDBCreators group, the OracleContextAdmins group, or you must be the directory superuser to perform this task.
|
Note: Remember the database wallet password you entered in Step 5. It cannot be retrieved after you finish database registration, but can be changed later by using Oracle Wallet Manager. See "About the Database Wallet and Password" for further information about this database wallet. |
If you must unregister a database from the directory, then use Database Configuration Assistant and follow the same steps used for registering it, except choose the unregister option. When you unregister a database from the directory, Database Configuration Assistant performs the following configuration tasks:
LDAP_DIRECTORY_ACCESS parameter to NONE.The database requires the wallet even if no SSL (Secure Sockets Layer) is used to secure the connection between the database and the directory. If SSL is used, then this wallet should be used to store the database's digital PKI certificate.
The wallet password you enter when using Database Configuration Assistant to register a database in the directory is the password to the wallet itself, and is not the database's directory login credentials.
You can change this wallet password later by using Oracle Wallet Manager. However, if you forget this wallet password, you must delete the database wallet that was created, unregister the database from the directory, and reregister the database in the directory so another database wallet can be generated.
| See Also:
Chapter 8, "Using Oracle Wallet Manager" for information about using Oracle Wallet Manager to change wallet passwords and, in general, to manage public key infrastructure (PKI) credentials. |
After you have prepared the directory for Enterprise User Security, then you can create the Enterprise User Security database and directory objects as described in "Configuring Enterprise User Security Objects in the Database and the Directory".
See Also:
|
This is the second phase of configuration steps required to implement Enterprise User Security. The configuration steps in this section assume the following recommended setup:
Note that databases must be in an enterprise domain that is in an identity management realm in order for enterprise user logins to work.
If you do not use the OracleDefaultDomain or store your users in an identity management realm Users subtree, then see the following documentation:
|
To configure Enterprise User Security objects in the database and directory perform the following tasks:
Although this step can also be completed by using Oracle Enterprise Manager, the following examples use SQL*Plus directly:
SQL> CREATE USER guest IDENTIFIED GLOBALLY AS '';
If you do not want to use a shared schema, then specify a user DN between the single quotation marks to create an exclusive schema.
CREATE SESSION privilege to the shared schema created in Step 1 so users can connect to it. The following syntax example grants the CREATE SESSION privilege to the guest shared schema:
SQL> GRANT CREATE SESSION TO guest;
Alternatively, you can grant the CREATE SESSION privilege to a global role, which you grant to specific users through an enterprise role. See Step 3.
emprole and custrole global roles:
SQL> CREATE ROLE emprole IDENTIFIED GLOBALLY; SQL> CREATE ROLE custrole IDENTIFIED GLOBALLY;
Global roles are associated with enterprise roles, which will be created later, and then are allocated to enterprise users.
SELECT privilege to emprole and custrole global roles on the products table:
SQL> GRANT select ON products TO custrole, emprole;
| See Also:
Oracle Database SQL Reference for information about the syntax used for these steps. |
Use Enterprise Security Manager (see "Starting Enterprise Security Manager") to configure user-schema mappings for the OracleDefaultDomain by using the following steps:
For more information about this task, see "Managing Enterprise Domain Database Schema Mappings".
|
Note: You also can create user-schema mappings under a database in an enterprise domain which only apply to that database. |
Use Enterprise Security Manager to create enterprise roles in the OracleDefaultDomain by using the following steps:
The Create Enterprise Role dialog box appears with the appropriate realm Oracle Context and enterprise domain displayed.
For more information about this task, see "Creating a New Enterprise Role".
Use Enterprise Security Manager to add the global database roles that you created in Task 1 to the enterprise roles that you created in Task 3 by using the following steps:
For more information about this task, see "Assigning Database Global Role Membership to an Enterprise Role".
Use Enterprise Security Manager to grant enterprise roles that you created in Task 3 to the enterprise users by using the following steps:
The Add Enterprise Users dialog box automatically closes and you are returned to the main application window.
For more information about this task, see "Granting Enterprise Roles to Users".
Based on the authentication method you have chosen, go to one of the following sections to complete your Enterprise User Security configuration:
| See Also:
Table 11-1, "Enterprise User Security Authentication: Selection Criteria" for a comparison of the benefits provided by password, Kerberos, and SSL authentication for Enterprise User Security. |
By default, new enterprise domains are configured to accept all supported user authentication types (password, Kerberos, and SSL). If you want enterprise users to be authenticated by passwords, then you must configure that as described in the following tasks.
The configuration steps in this section assume the following:
ldap.ora, also ensure that the port number for this SSL with no authentication instance is listed there as your directory SSL port.To configure Enterprise User Security for password authentication, perform the following tasks:
By default, the OracleDefaultDomain is configured to accept password authentication. If this has been changed, then use Enterprise Security Manager to enable password authentication for the OracleDefaultDomain and add it to the Password-Accessible Domains List by using the following steps:
For more information about this task, see "Managing Password Accessible Domains".
Use Enterprise Security Manager to add the OracleDefaultDomain to the Password-Accessible Domains List by using the following steps:
For more information about this task, see "Managing Password Accessible Domains".
For an enterprise user whose directory login name is hscortea and whose password is welcome, enter the following to connect to the database by using SQL*Plus:
SQL> connect hscortea/welcome@<Oracle Net Service Name>
The database authenticates the enterprise user (hscortea) by verifying the username/password combination against the directory entry associated with this user. Then it identifies the proper schema and retrieves the user's global roles. If successful, the connection to the database is established.
If your connection succeeds, then the system responds Connected to:.... This is the confirmation message of a successful connect and setup. If an error message displays, then see "ORA-# Errors for Password-Authenticated Enterprise Users".
If you do connect successfully, then check that the appropriate global roles were retrieved from the directory by entering the following at the SQL*Plus prompt:
select * from session_roles
If the global roles were not retrieved from the directory, then see "NO-GLOBAL-ROLES Checklist".
You have completed password-authenticated Enterprise User Security configuration.
See Also:
|
The configuration steps in this section assume the following:
ldap.ora, also ensure that the port number for this SSL with no authentication instance is listed there as your directory SSL port.To configure Enterprise User Security for Kerberos authentication, perform the following tasks:
Use Oracle Internet Directory Self-Service Console to configure the Enterprise Security Manager Console to display the Kerberos principal name attribute. For more information about this task, see "Configuring Enterprise Security Manager Console for Kerberos-Authenticated Enterprise Users".
Use Enterprise Security Manager Console to enter the directory attribute used to store the Kerberos principal name for the identity management realm you are using in the directory. By default Kerberos principal names are stored in the krbPrincipalName attribute, but can be changed to correspond to your directory configuration by changing orclCommonKrbPrincipalAttribute in the identity management realm. For more information about this task, see "Setting Login Name, Kerberos Principal Name, User Search Base, and Group Search Base Identity Management Realm Attributes".
|
Note: By default, Enterprise Security Manager Console user interface does not display the field where you can configure Kerberos principal names. The first time you create Kerberos-authenticated users in the directory, you must configure the console to display the |
Use Enterprise Security Manager Console to specify the enterprise user's Kerberos principal name (Kerberos_username@Kerberos_realm) in the krbPrincipalName attribute of the enterprise user's directory entry. For more information about this task, see "Creating New Enterprise Users".
By default, the OracleDefaultDomain is configured to accept all types of authentication. If this has been changed, or you are using another domain then use Enterprise Security Manager to enable Kerberos authentication for your enterprise domain by using the following steps:
For more information about this task, see "Managing Database Security Options for an Enterprise Domain".
If the KDC is not part of the operating system, such as Kerberos V5 from MIT, then the user must get an initial ticket with the FORWARDABLE flag set by using the okinit utility. See "Obtaining the Initial Ticket with the okinit Utility".
If the KDC is part of the operating system, such as Windows 2000 or some versions of Linux or UNIX, then the operating system automatically picks up the user's ticket (with the FORWARDABLE flag set) from the cache when the user logs in.
The user connects to the database by launching SQL*Plus and entering the following at the command line:
SQL> connect /@<net_service_name>
The database uses Kerberos to authenticate the user. The database authenticates itself to the directory by password.
If your connection succeeds, then the system responds Connected to:.... This is the confirmation message of a successful connect and setup. If an error message displays, then see "ORA-# Errors for Kerberos-Authenticated Enterprise Users".
If you do connect successfully, then check that the appropriate global roles were retrieved from the directory by entering the following at the SQL*Plus prompt:
select * from session_roles
If the global roles were not retrieved from the directory, then see "NO-GLOBAL-ROLES Checklist".
You have completed Kerberos-authenticated Enterprise User Security configuration.
See Also:
|
The configuration steps in this section assume the following:
See "Viewing the Database DN in the Wallet and in the Directory". Note that Database Configuration Assistant sets the database directory entry DN and the database wallet DN to be identical when registering the database in the directory.
To configure Enterprise User Security for SSL authentication, perform the following tasks:
Use Enterprise Security Manager to enable SSL authentication for the enterprise domain (OracleDefaultDomain) by using the following steps:
For more information about this task, see "Managing Database Security Options for an Enterprise Domain".
You can change this initialization parameter either by editing your database initialization parameter file, or by issuing an ALTER SYSTEM SQL command with the SET clause.
For example, the following ALTER SYSTEM command changes the LDAP_DIRECTORY_ACCESS parameter value to SSL in the server parameter file:
ALTER SYSTEM SET LDAP_DIRECTORY_ACCESS=SSL SCOPE=SPFILE
See Also:
|
Connecting as an SSL-authenticated enterprise user involves ensuring that you have the appropriate Oracle wallet features configured, and that you do not have a wallet location specified in the client sqlnet.ora file. If the client sqlnet.ora file contains a wallet location, then multiple users cannot share that file. Only the server sqlnet.ora file must have a value for the wallet location parameter.
To connect as an SSL-authentication enterprise user, perform the following steps:
.sso) file and enables authentication to the SSL adapter. See "Using Auto Login".TNS_ADMIN environment variable (to point to the client's sqlnet.ora file) for the client if the client Oracle home points to a server Oracle home. (Because a server must have a wallet location set in its sqlnet.ora file and a client cannot have a wallet location specified there, the server and client cannot share sqlnet.ora files.)
If you have a separate client Oracle home, then you do not need to set the TNS_ADMIN environment variable.
SQL> /@connect_identifier
where connect_identifer is the Oracle Net service name you set up when you configured SSL for the database client.
If your connection succeeds, then the system responds Connected to:.... This is the confirmation message of a successful connect and setup. If an error message displays, then see "ORA-# Errors for SSL-Authenticated Enterprise Users".
If you do connect successfully, then check that the appropriate global roles were retrieved from the directory by entering the following at the SQL*Plus prompt:
select * from session_roles
If the global roles were not retrieved from the directory, then see "NO-GLOBAL-ROLES Checklist".
You have completed SSL-authenticated Enterprise User Security configuration.
|
Note: For security purposes, ensure that you disable auto login for the user wallet after logging out from the enterprise user session with the database. This is especially important if the client machine is shared by more than one user. See "Disabling Auto Login" for information about disabling this Oracle Wallet feature. |
For SSL-authenticated Enterprise User Security to work, the database DNs in the database wallet, the database directory entry, and the database certificate must be identical. When you use Database Configuration Assistant to register your database in the directory, this tool automatically creates identical DNs for the database wallet and the database directory entry. To request a database certificate with the proper DN, you must view either the directory entry DN or the wallet DN.
cn=<short_database_name>,cn=OracleContext,<realm_DN> where short_database_name is the first part of the fully qualified domain name for a database. For example, if you have a database named db1.us.oracle.com, then the short database name is db1.mkstore utility syntax on the command line:
mkstore -wrl <wallet_location> -viewEntry ORACLE.SECURITY.DN
where wallet_location is the path to the database wallet.
See Also:
|
Current user database links require SSL-enabled network connections between the databases. Before you can enable current user database links, you must enable SSL, create Oracle wallets, and obtain PKI credentials for all databases involved.
Then use Enterprise Security Manager to enable current user database links between databases within the enterprise domain in the directory by using the following steps:
For more information about this task, see "Managing Database Security Options for an Enterprise Domain".
This section describes potential problems and associated corrective actions in the following topics:
If you receive an ORA-# error while using password-authenticated Enterprise User Security, then locate the error in the following section and take the recommended action.
Action: See "USER-SCHEMA ERROR Checklist"
Cause: Indicates a problem with the connection between the database and the directory.
Action: Check the following:
wallet_location value in the database's sqlnet.ora file. If not, then use Oracle Net Manager to enter one.ldap.ora file in $LDAP_ADMIN, $ORACLE_HOME/ldap/admin, $TNS_ADMIN, or $ORACLE_HOME/network/admin. (See Oracle Internet Directory Administrator's Guide for information about DNS server discovery.)ldap.ora file) supports SSL with no authentication.LDAP_DIRECTORY_ACCESS parameter is set to PASSWORD in the database initialization parameters file.cwallet.sso file in $ORACLE_HOME/admin/<ORACLE_SID>/wallet/.mkstore command line utility to retrieve the database password from the wallet by using the following syntax:
mkstore -wrl <database wallet location> -viewEntry ORACLE.SECURITY.PASSWORD
mkstore in the following ldapbind:
ldapbind -h <directory host> -p <non-SSL directory port> -D "<database DN>" -w <password returned by mkstore>
Action: Check the following:
verifierServices group has read permission on the user entry, and that this permission is not prevented by an ACL between the User Search Base entry and the user entry in the directory tree.Action: Use Enterprise Security Manager to set the user authentication policy for this enterprise domain to Password or ALL.
Action: Check the following:
Action: Check the following:
orcluser object class. If it does not, then perform the following steps:
orcluser, and thenorcluser and the orcluserV2 object classes.orclpassword in the user entry. If there is no value, then reset the user's directory password (userpassword attribute). This should prompt Oracle Internet Directory to regenerate the database password verifier for the user.orclpassword attributes by the verifierServices group. This is set properly by default, but may have been altered.Cause: There are multiple user DNs in the directory within the user search base whose login name for the user matches what was provided during the database connection.
Action: Use Enterprise Security Manager Console to make the login name value unique (no two users share the same login name) within all user search bases associated with the realm Oracle Context.
Action: Check that the relevant directory instance is up and running.
Cause: The database cannot read the enterprise domain information that it needs.
Action: See "DOMAIN-READ-ERROR Checklist"
Action: Check that you are using a non-SSL connect string.
If you receive an ORA-# error while using Kerberos-authenticated Enterprise User Security, then locate the error in the following section and take the recommended action.
Action: See "USER-SCHEMA ERROR Checklist"
Cause: Indicates a problem with the connection between the database and the directory.
Action: See the actions listed for resolving "ORA-28030: Problem accessing LDAP directory service" in the troubleshooting section for password-authenticated enterprise users.
Action: See the actions listed for resolving "ORA-28271: No permission to read user entry in LDAP directory service" in the troubleshooting section for password-authenticated enterprise users.
Action: Perform the following actions:
Cause: The Kerberos principal name for this user is not unique within the user search base containing this user.
Action: Use Oracle Internet Directory Self-Service Console to change the Kerberos principal name, or to change the other copies so that it is unique.
Action: Check the following:
krbprincipalname attribute.
If it does not have the krbprincipalname attribute, then check the following:
krbprincipalname, and thenorclcommonattributes object class.krbprincipalname in the user entry. If there is no value, then use Oracle Internet Directory Self-Service Console to enter one.krbprincipalname attributes by the verifierServices group. This is set properly by default, but may have been altered.Action: Check the following:
ldapsearch to check that a user search base containing this user is listed in the identity management realm that you are using.Action: Check that the database wallet contains the correct credentials for the database-to-directory connection. The wallet DN should be the DN of the database in Oracle Internet Directory. To retrieve the credentials, perform the following steps:
mkstore command line utility to retrieve the database password for the wallet by using the following syntax:
mkstore -wrl <database wallet location> -viewEntry ORACLE.SECURITY.PASSWORD -viewEntry ORACLE.SECURITY.DN
mkstore in the following ldapbind:
ldapbind -h <directory host> -p <non-SSL directory port> -D "<database DN>" -w <password>
Action: Check that the user entry is present in the directory.
If you receive an ORA-# error while using SSL-authenticated Enterprise User Security, then locate the error in the following section and take the recommended action.
Action: See "USER-SCHEMA ERROR Checklist"
Cause: Indicates a problem with the connection between the database and the directory.
Action: Check the following:
wallet_location value in the database's sqlnet.ora file. If not, then use Oracle Net Manager to enter one.ldap.ora file in $LDAP_ADMIN, $ORACLE_HOME/ldap/admin, $TNS_ADMIN, or $ORACLE_HOME/network/admin. (See Oracle Internet Directory Administrator's Guide for information about DNS server discovery.)ldap.ora file) supports SSL with two-way authentication.LDAP_DIRECTORY_ACCESS parameter is set to SSL in the database initialization parameters file.cwallet.sso file in $ORACLE_HOME/admin/<ORACLE_SID>/wallet/.mkstore command line utility to check that the database wallet has the database DN in it by using the following syntax:
mkstore -wrl <database_wallet_location> -viewEntry ORACLE.SECURITY.DN
If the wallet does not contain the database DN, then use Database Configuration Assistant to re-register the database with Oracle Internet Directory.
ldapbind:
ldapbind -h <directory_host> -p <directory_SSLport> -U 3 -W "file:<database wallet_location>" -P <wallet_password>
Action: Use Enterprise Security Manager to set the user authentication policy for this enterprise domain to include SSL.
Action: See Chapter 7, "Configuring Secure Sockets Layer Authentication" for information about configuring your SSL connection.
If the enterprise user can connect to the database, but a select * from session_roles returns no global roles, then check the following:
CREATE ROLE <role_name> IDENTIFIED GLOBALLY;
If your database cannot read the user schema, then check the following:
CREATE USER username IDENTIFIED GLOBALLY AS ' ';
or by using the following syntax:
CREATE USER username IDENTIFIED GLOBALLY AS '<DN>';
CREATE USER username IDENTIFIED GLOBALLY AS '<user_DN>'; syntax), andThen ensure that the DN in the user wallet matches the DN that was used in the CREATE USER statement.
Use Oracle Wallet Manager to view the DN in the user wallet.
Use the following syntax to view the DN that was used with the CREATE USER statement:
SELECT EXTERNAL_NAME FROM DBA_USERS WHERE USERNAME='<schema>';
To check this, enter the following ldapsearch command for your database-to-directory connection type:
ldapsearch -h <directory_host> -p <directory_SSLport> -U 3 -W "file:<database_wallet_path>" -P <wallet_password> -b "<database_ DN>" "objectclass=*"
where <wallet_password> is the password to the wallet, which enables you to open or change the wallet.
ldapsearch -h <directory_host> -p <> -D <database_DN> -w <database_directory_password> -b "<database_DN>" "objectclass=*"
where <database_directory_password> is the password in the database wallet, which is the database's password to Oracle Internet Directory.
You should see the database entry and the relevant mapping.
If your database cannot read its enterprise domain information in Oracle Internet Directory, then check the following:
ldapsearch -h <directory_host> -p <directory_SSLport> -U 3 -W "file:<database_wallet_path>" -P <wallet_password> -b "cn=OracleContext, <realm_DN>" "objectclass=orclDBEnterpriseDomain"
where <wallet_password> is the password to the wallet, which enables you to open or change the wallet.
ldapsearch -h <directory_host> -p <directory_port> -D <database_DN> -w <database_directory_password> -b "cn=OracleContext, <realm_DN>" "objectclass=orclDBEnterpriseDomain"
where <database_directory_password> is the password in the database wallet, which is the database's password to Oracle Internet Directory.
This ldapsearch should return exactly one enterprise domain.
If no domain is returned, and Enterprise Security Manager shows the database as a member of a domain, then restart the database. Restarting the database updates the cached value for the enterprise domain.
If more than one domain is returned, then use Enterprise Security Manager to remove the database from the additional domain.
ldapsearch -h <directory_host> -p <directory_SSLport> -U 3 -W "file:<database_wallet_path>" -P <wallet_password> -b "cn=OracleContext, <realm_DN>" "objectclass=orclDBEnterpriseRole"
where <wallet_password> is the password to the wallet, which enables you to open or change the wallet.
ldapsearch -h <directory_host> -p <directory_port> -D <database_DN> -w <database_directory_password> -b "cn=OracleContext, <realm_DN>" "objectclass=orclDBEnterpriseRole"
where <database_directory_password> is the password in the database wallet, which is the database's password to Oracle Internet Directory.
This ldapsearch should return all of the enterprise roles that you have created for this domain. If it does not, then use Enterprise Security Manager to create enterprise roles and mappings.