Release 2 (9.2)
Part Number A96573-01
Home |
Book List |
Contents |
Index |
 Master Index |
 Feedback |
| Oracle Advanced Security Administrator's Guide Release 2 (9.2) Part Number A96573-01 |
|
This chapter describes how to use the Secure Sockets Layer (SSL) protocol in Oracle Advanced Security. It contains the following topics:
Secure Sockets Layer (SSL) is an industry standard protocol designed by Netscape Communications Corporation for securing network connections. SSL uses RSA public key cryptography to provide authentication, encryption, and data integrity in a public key infrastructure (PKI).
This section discusses the following topics:
Oracle Advanced Security supports authentication by using digital certificates over SSL in addition to the native encryption and data integrity capabilities of the SSL protocol.
By using Oracle Advanced Security SSL functionality to secure communications between clients and servers, you can
You can use SSL features by themselves or in combination with other authentication methods supported by Oracle Advanced Security. For example, you can use the encryption provided by SSL in combination with the authentication provided by Kerberos. SSL supports any of the following authentication modes:
See Also:
|
The components of SSL in an Oracle environment include the following:
A certificate authority (CA) is a trusted third party that certifies the identity of third parties and other entities, such as users, databases, administrators, clients, and servers. The certificate authority verifies the party identity and grants a certificate, signing it with its private key.
Different CAs may have different identification requirements when issuing certificates. One may require the presentation of a user's driver's license, while others may require notarization of the certificate request form, or fingerprints of the requesting party.
The CA publishes its own certificate, which includes its public key. Each network entity has a list of certificates of the CAs it trusts. Before communicating with another entity, a given entity uses this list to verify that the signature on the other entity's certificate is from a known, trusted CA.
Network entities can obtain their certificates from the same or different CAs. By default, Oracle Advanced Security automatically installs trusted certificates from VeriSign, RSA, Entrust, and GTE CyberTrust when you install a new wallet.
A certificate is created when a party's public key is signed by a trusted certificate authority (CA). A certificate ensures that a party's identification information is correct, and that the public key actually belongs to that party.
A certificate contains the party's name, public key, and an expiration date--as well as a serial number and certificate chain information. It can also contain information about the privileges associated with the certificate.
When a network entity receives a certificate, it verifies that it is a trusted certificate--one issued and signed by a trusted certificate authority. A certificate remains valid until it expires or until it is terminated.
A wallet is a container that is used to store authentication and signing credentials, including private keys, certificates, and trusted certificates needed by SSL. In an Oracle environment, every entity that communicates over SSL must have a wallet containing an X.509 version 3 certificate, private key, and list of trusted certificates.
Security administrators use the Oracle Wallet Manager to manage security credentials on the server. Wallet owners use it to manage security credentials on clients. Specifically, you use Oracle Wallet Manager to do the following:
|
Note: Installation of Oracle Advanced Security Release 2 (9.2) also installs Oracle Wallet Manager release 3.0 and Oracle Enterprise Login Assistant release 9.2. |
When a network connection over SSL is initiated, the client and server perform an SSL handshake that includes the following steps:
In an Oracle environment, the authentication process consists of the following steps:
You can use the Oracle Advanced Security SSL feature to secure connections between non-Oracle clients and Oracle database servers. For example, SSL can grant secure access to a browser client outside an Oracle network to authorized data within the Oracle network.
Figure 7-1 shows how SSL is used to secure connections between Oracle and non-Oracle entities over the Internet. In this example, a Web server runs as an Oracle9i Java client. It receives messages over HTTPS (HTTP secured by SSL), and sends CORBA requests to the Oracle database server over IIOP/SSL (IIOP secured by SSL). In this example, the Web server passes its own certificate to the Oracle server, rather than the certificate of the Web client.
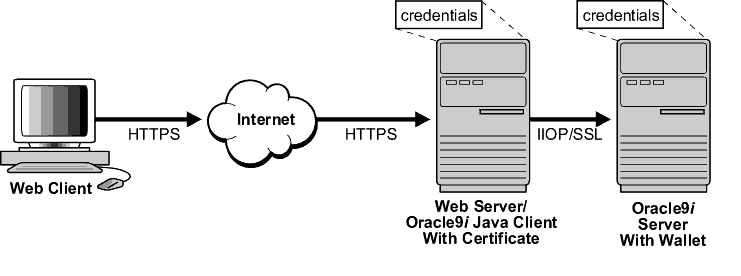
Text description of the illustration ano81017.gif
You can configure Oracle Advanced Security to use SSL concurrently with other supported authentication methods, such as Kerberos, RADIUS, or CyberSafe, which are discussed in the following sections:
| See Also:
Appendix A"Data Encryption and Integrity Parameters" for information about how to configure SSL with other supported authentication methods, including an example of a |
Figure 7-2, which displays the Oracle Advanced Security implementation architecture, shows that Oracle Advanced Security operates at the session layer on top of SSL and uses TCP/IP at the transport layer. This separation of functionality lets you employ SSL concurrently with other supported protocols.
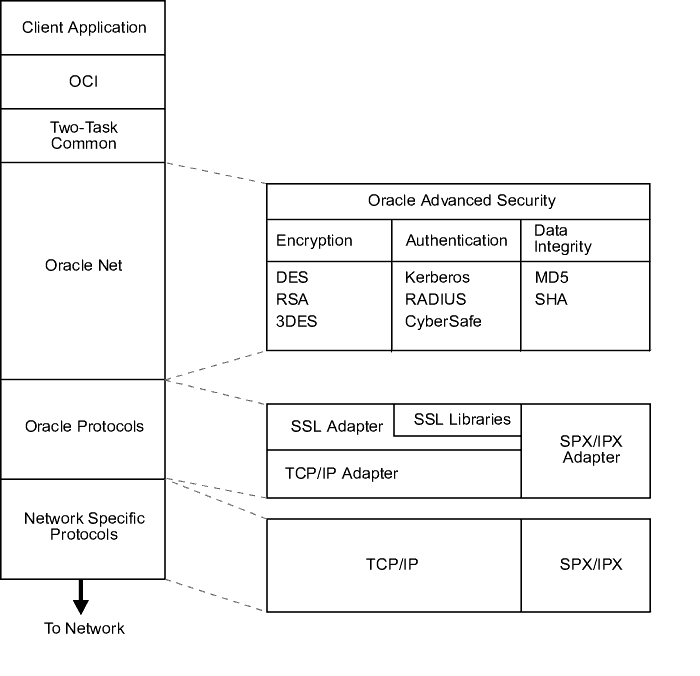
Text description of the illustration ano81015.gif
| See Also:
Oracle9i Net Services Administrator's Guide, for information about stack communications in an Oracle networking environment |
Figure 7-3 illustrates a configuration in which SSL is used in combination with another authentication method supported by Oracle Advanced Security. In this example, SSL is used to establish the initial handshake (server authentication), and an alternative authentication method is used to authenticate the client.
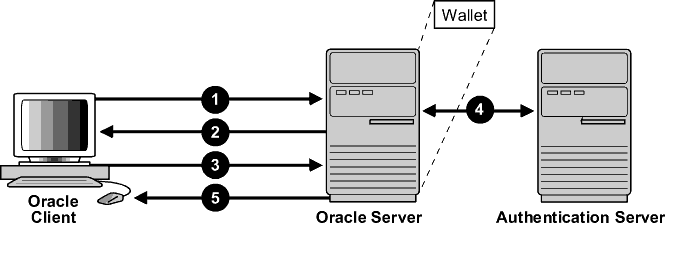
Text description of the illustration ano81018.gif
Oracle Advanced Security supports two types of firewalls:
When you enable SSL, stateful inspection firewalls behave like application proxy firewalls because they do not decrypt encrypted packets.
Firewalls do not inspect encrypted traffic. When a firewall encounters data addressed to an SSL port on an intranet server, it checks the target IP address against its access rules and lets the SSL packet pass through to permitted SSL ports, rejecting all others.
With the Oracle Net Firewall Proxy kit, firewall applications can provide specific support for database network traffic. If the proxy kit is implemented in the firewall, the following processing takes place:
Oracle Connection Manager lets you route client connections over multiple Net Manager protocols. Each client connection request establishes an SSL connection between the client and Oracle Connection Manager, which in turn establishes a TCP/IP connection with the target database. Multiple clients can thus connect to multiple databases behind the firewall, using a single SSL port through the firewall.
Consider the following issues when using SSL:
|
Note:
|
See Also:
|
To enable SSL:
Install Oracle Advanced Security on both the client and server. When you do this, the Oracle Universal Installer automatically installs SSL libraries, Oracle Wallet Manager, and Oracle Enterprise Login Assistant on your system.
To configure SSL on the client:
| See Also:
Appendix B, "Authentication Parameters", for the dynamic parameter names. |
Before proceeding with the next step, you must confirm that a wallet has been created.
See Also:
|
This step contains the following two parts:
Step 2a. To configure the service name to include server DNs
Oracle Advanced Security Release 2 (9.2) matches the server's global database name against the distinguished name (DN) from the server certificate. This protects against the threat of connections to a server potentially faking its identity, where the server has a valid X.509 v3 certificate, but not the proper certificate for the respective database.
To enable DN matching against server certificates, you must manually edit the tnsnames.ora file to specify the server's DN by defining the SSL_SERVER_CERT_DN parameter. The client uses this information to obtain the list of DNs it expects for each of the servers, enforcing the server's DN to match its service name. Example 7-1 shows an entry for the Finance database in the tnsnames.ora file.
finance=
(DESCRIPTION=
(ADDRESS_LIST=
(ADDRESS= (PROTOCOL = tcps) (HOST =finance_server) (PORT =1575)))
(CONNECT_DATA=
(SERVICE_NAME= Finance.us.acme.com))
(SECURITY=
(SSL_SERVER_CERT_DN="cn=finance,cn=OracleContext,c=us,o=acme"))
The tnsnames.ora file can be located on the client or in the LDAP directory.
Alternatively, the administrator can ensure that DNs in the certificates from a trusted certificate authority have a common name (CN) that matches the service name.
|
Note: Oracle Corporation recommends that you use Oracle Wallet Manager to remove the trusted certificate in your Oracle wallet associated with each certificate authority that you do not use. |
See Also:
|
Step 2b. To configure the service name to use TCP/IP with SSL
Example 7-1 also shows an entry that specifies TCP/IP with SSL as the connecting protocol in the tnsnames.ora file. To specify TCP/IP with SSL, you must enter tcps as the PROTOCOL in the ADDRESS parameter of the tnsnames.ora file. In addition, you must enter the same information in the ADDRESS parameter of the listener.ora file. Example 7-2 shows an entry that specifies TCP/IP with SSL as the protocol.
LISTENER= (DESCRIPTION_LIST=
(DESCRIPTION=
(ADDRESS= (PROTOCOL = tcps) (HOST = finance_server) (PORT = 1575))))
Alternatively, the administrator can use Oracle Net Manager to configure TCP/IP with SSL.
To specify required configuration parameters for the client:
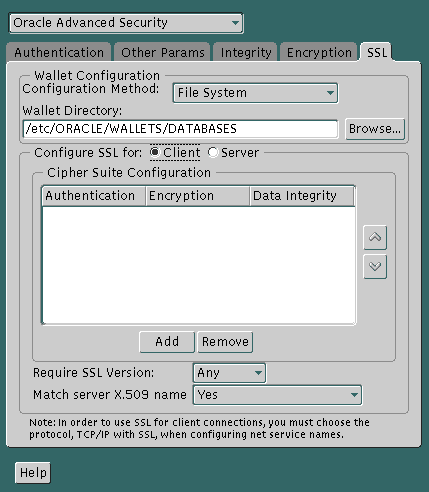
Text description of the illustration ssl0001.gif
|
Important:
Be sure to enter the same wallet location when you create it and when you set the location in the |
The sqlnet.ora file on the client is updated with the following entries:
SSL_CLIENT_AUTHENTICATION =TRUE
wallet_location =
(SOURCE=
(METHOD=File)
(METHOD_DATA=
(DIRECTORY=wallet_location)))
SSL_SERVER_DN_MATCH=(ON/OFF)
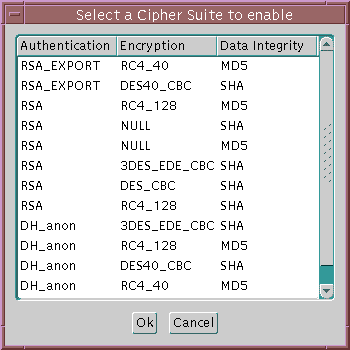
A cipher suite is a set of authentication, encryption, and data integrity algorithms used for exchanging messages between network entities. During an SSL handshake, two entities negotiate to see which cipher suite they will use when transmitting messages back and forth.
When you install Oracle Advanced Security, several SSL cipher suites are set for you by default. You can override the default by setting the SSL_CIPHER_SUITES parameter. For example, if you use Oracle Net Manager to add the cipher suite SSL_RSA_WITH_RC4_128_SHA, all other cipher suites in the default setting are ignored.
You can prioritize the cipher suites. When the client negotiates with servers regarding which cipher suite to use, it follows the prioritization you set. When you prioritize the cipher suites, consider the following:
The cipher suites selected for a client must be compatible with those required by the server. For example, in the case of an Oracle Call Interface (OCI) user, the server requires the client to authenticate itself. You cannot, in this case, use a cipher suite employing Diffie-Hellman anonymous authentication which disallows the exchange of certificates. By contrast, in the case of an Enterprise JavaBeans (EJB) user, the server does not require the client to authenticate itself. In this case, you can use Diffie-Hellman anonymous authentication.
You typically prioritize cipher suites starting with the strongest and moving to the weakest.
Table 7-1 lists the SSL cipher suites supported in the current release of Oracle Advanced Security. These cipher suites are set by default when you install Oracle Advanced Security. This table also lists the authentication, encryption, and data integrity types each cipher suite uses.
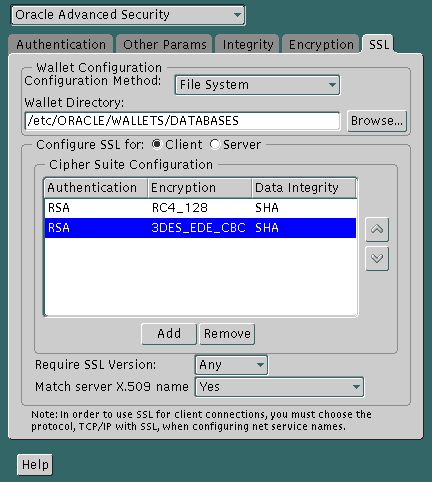
The sqlnet.ora file is updated with the following entry:
SSL_CIPHER_SUITES= (SSL_cipher_suite1 [,SSL_cipher_suite2])
You can set the SSL_VERSION parameter in the sqlnet.ora file. This parameter defines the version of SSL that must run on the systems with which the client communicates. You can require these systems to use SSL 3.0, or any valid, future version. The default setting for this parameter in sqlnet.ora is undetermined, which is set by selecting Any from the list in the SSL tab of the Oracle Advanced Security window.
The sqlnet.ora file is updated with the following entry:
SSL_VERSION=UNDETERMINED
The SQLNET.AUTHENTICATION_SERVICES parameter in the sqlnet.ora file sets the SSL authentication service.
Set this parameter if you want to use SSL authentication in conjunction with another authentication method supported by Oracle Advanced Security. For example, use this parameter if you want the server to authenticate itself to the client by using SSL and the client to authenticate itself to the server by using Kerberos.
To set the SQLNET.AUTHENTICATION_SERVICES parameter:
Add TCP/IP with SSL (TCPS) to this parameter in the sqlnet.ora file by using a text editor. For example, if you want to use SSL authentication in conjunction with RADIUS authentication, set this parameter as follows:
SQLNET.AUTHENTICATION_SERVICES = (TCPS, radius)
If you do not want to use SSL authentication in conjunction with another authentication method, then do not set this parameter.
During installation, Oracle sets defaults on both the Oracle database server and on the Oracle client for all SSL parameters except the location of the Oracle wallet. To configure SSL on the server, perform these steps:
| See Also:
Appendix B, "Authentication Parameters" for the dynamic parameter names |
Before proceeding with the next step, you must confirm that a wallet has been created.
See Also:
|
To specify required configuration parameters for the server:
|
Important:
Be sure to enter the same wallet location when you create it and when you set the location in the |
The sqlnet.ora and listener.ora files are updated with the following entries:
wallet_location =
(SOURCE=
(METHOD=File)
(METHOD_DATA=
(DIRECTORY=wallet_location)))
A cipher suite is a set of authentication, encryption, and data integrity algorithms used for exchanging messages between network entities. During an SSL handshake, two entities negotiate to see which cipher suite they will use when transmitting messages back and forth.
When you install Oracle Advanced Security, several SSL cipher suites are set for you by default. You can override the default by setting the SSL_CIPHER_SUITES parameter. For example, if you use Oracle Net Manager to add the cipher suite SSL_RSA_WITH_RC4_128_SHA, all other cipher suites in the default setting are ignored.
You can prioritize the cipher suites. When the client negotiates with servers regarding which cipher suite to use, it follows the prioritization you set. When you prioritize the cipher suites, consider the following:
The cipher suites selected for a server must be compatible with those required by the client.
You typically prioritize cipher suites starting with the strongest and moving to the weakest.
|
Note: In Oracle Advanced Security Release 2 (9.2), if you set a cipher suite employing Diffie-Hellman anonymous authentication on the server, you must also set the same cipher suite on the client. Otherwise, the connection fails. If you use a cipher suite employing Diffie-Hellman anonymous, you must set the SSL_CLIENT_AUTHENTICATION parameter to FALSE. See: Step 5: Set SSL Client Authentication (Optional). |
Table 7-1 lists the SSL cipher suites supported in the current release of Oracle Advanced Security. These cipher suites are set by default when you install Oracle Advanced Security. This table also lists the authentication, encryption, and data integrity types each cipher suite uses.
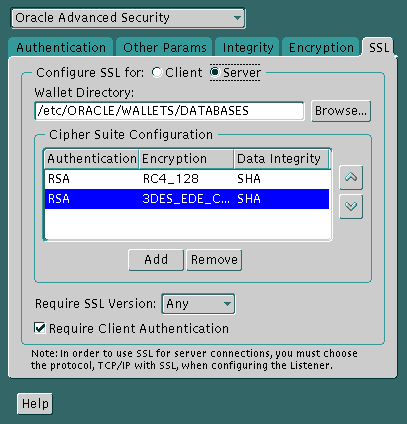
Text description of the illustration ssl0004.gif
The sqlnet.ora file is updated with the following entry:
SSL_CIPHER_SUITES= (SSL_cipher_suite1 [,SSL_cipher_suite2])
You can set the SSL_VERSION parameter in the sqlnet.ora file. This parameter defines the version of SSL that must run on the systems with which the client communicates. You can require these systems to use SSL 3.0, or any valid, future version. The default setting for this parameter in sqlnet.ora is undetermined, which is set by selecting Any from the list in the SSL tab of the Oracle Advanced Security window.
The sqlnet.ora file is updated with the following entry:
SSL_VERSION=UNDETERMINED
The SSL_CLIENT_AUTHENTICATION parameter in the sqlnet.ora file controls whether the client is authenticated using SSL. The default value is TRUE.
You must set this parameter to FALSE if you are using a cipher suite that contains Diffie-Hellman anonymous authentication (DH_anon). Also, you can set this parameter to FALSE for the client to authenticate itself to the server by using any of the non-SSL authentication methods supported by Oracle Advanced Security, such as Kerberos or CyberSafe.
To set this parameter to FALSE:
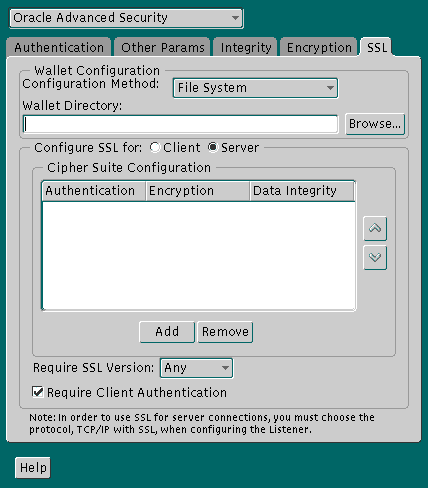
Text description of the illustration ssl0005.gif
The sqlnet.ora file is updated with the following entry:
SSL_CLIENT_AUTHENTICATION=FALSE
The SQLNET.AUTHENTICATION_SERVICES parameter in the sqlnet.ora file sets the SSL authentication service.
Set this parameter if you want to use SSL authentication in conjunction with another authentication method supported by Oracle Advanced Security. For example, use this parameter if you want the server to authenticate itself to the client by using SSL and the client to authenticate itself to the server by using Kerberos.
To set the SQLNET.AUTHENTICATION_SERVICES parameter:
Add TCP/IP with SSL (TCPS) to this parameter in the sqlnet.ora file by using a text editor. For example, if you want to use SSL authentication in conjunction with RADIUS authentication, set this parameter as follows:
SQLNET.AUTHENTICATION_SERVICES = (TCPS, radius)
If you do not want to use SSL authentication in conjunction with another authentication method, then do not set this parameter.
Configure the listener with a TCP/IP with SSL listening endpoint in the listener.ora file. Oracle Corporation recommends a port number 2484 for typical Oracle Net clients and 2482 for client connections to Oracle9i JServer.
If you are using SSL authentication, launch SQL*Plus and enter the following:
CONNECT/@dnet_service_name
If you are not using SSL authentication, launch SQL*Plus and enter the following:
CONNECT username/password@net_service_name
SSL handshake operations make heavy processing demands on a system, which may result in slower server and transaction performance. SSL hardware accelerators offload SSL processing from the server, freeing the CPU to respond to other transactions. Oracle Advanced Security uses nCipher BSAFE Hardware APIs (BHAPI), to support SSL hardware acceleration. Using this interface, Oracle integrates with nCipher secure accelerators.
|
Note: You must contact your nCipher representative to obtain the certified versions of nCipher cards and software. |
To use an nCipher Secure Accelerator, you need the following components:
To use the secure accelerator, you must place the path to the directory that contains the nCipher BHAPI library in the following locations:
This enables the library to be loaded at runtime. Typically, the nCipher card is installed at the following locations:
The nCipher BHAPI library is in the directory where the secure accelerator is installed at the following location:
/toolkits/nfbhapi/
To detect whether the nCipher accelerator is being used, you can turn on SQL*Net tracing. If nCipher software is being used, then you will see the following entries in the SQL*Net tracing file without error messages logged between entry and exit:
nzos_initbhapi: entry nzos_initbhapi: exit
If error messages are logged between the entry and exit entries in the SQL*Net tracing file, then check the following list of possible error messages for information about how to resolve them.
Cause: The system cannot locate the nCipher BHAPI library.
Action: Ensure that the directory which contains the nCipher BHAPI library is present in the user's system path.
| See Also:
"Configuring Oracle Advanced Security To Use an nCipher Secure Accelerator" for information about where to include the path to the nCipher BHAPI library in the user's system path. |
Cause: The nCipher secure accelerator may not be running.
Action: Ensure that the secure accelerator is up by running the /bin/enquiry utility from the directory where the nCipher card is installed.
|
Note: The nCipher log file is in the directory where the secure accelerator is installed at the following location:
|
|
 Copyright © 1996, 2002 Oracle Corporation. All Rights Reserved. |
|