Release 2 (9.2)
Part Number A96582-01
Home |
Book List |
Contents |
Index |
 Master Index |
 Feedback |
| Oracle9i Security Overview Release 2 (9.2) Part Number A96582-01 |
|
Many security advantages can be had by centralizing in a directory the storage and management of user information such as identity, credentials, and other attributes. This chapter describes how to protect a directory, and how access can be controlled using a directory.
Administrators today must manage complex user information, keeping it current and secure. These tasks become all the more challenging with increased use of technology and a high user turnover in enterprises. For example, in a typical enterprise, each user can have multiple accounts on different databases. This means too many passwords for users to remember, and too many accounts for administrators to manage. Consequently, users write down their passwords, make them easy to remember (and easy for someone else to guess), or choose the same password for all accounts.
Administrators must manage multiple accounts for every user. As a result, they devote significant resources to user administration. Common information used by multiple applications--such as username, user's office location and phone number, and system privileges--is often fragmented across the enterprise, leading to data that is redundant, inconsistent, and expensive to manage.
There are security problems as well. For example, any time a user leaves a company or changes jobs, his privileges should change the same day in order to guard against misuse of his old or unused accounts and privileges. However, in a large enterprise, with user accounts and passwords distributed over multiple databases, an administrator may not be able make all the changes as expeditiously as good security requires.
Enterprise user security management must address these user, administration, and security challenges. The best way is to centralize storage and management of user-related information in an LDAP-compliant directory service such as Oracle Internet Directory. Then, when an employee changes jobs, the administrator needs to modify information in only one location--the directory. This centralization lowers the cost of administration and makes the enterprise more secure.
Today, network information is stored in multiple systems and in multiple directory formats. With new requirements for Internet computing and new e-business technologies, there is a growing need for a common repository infrastructure to serve as a foundation for management and configuration of all data and resources. Such a common infrastructure reduces the cost of managing and configuring resources in heterogeneous networks.
Lightweight Directory Access Protocol (LDAP) technology was initially developed at the University of Michigan. It is currently an industry-accepted standard and is available in a variety of implementations.
Support of LDAP-compliant directory servers provides a centralized vehicle for managing and configuring a distributed network. The directory can act as a central repository for all data on database network components, user and corporate policies, and user authentication and security, thus replacing client-side and server-side localized tnsnames.ora files.
An LDAP-compliant directory can provide many powerful features to protect information:
To gain all these advantages of security directory integration, you must first ensure that the directory itself is secure. This involves:
Once your directory has been secured, other applications in an enterprise or hosted environment can take advantage of all these features. They can use the directory for administrative delegation, and control access to application metadata.
This section describes how access can be controlled within the directory.
Authentication is the process by which the directory server establishes the true identity of the user connecting to the directory. To verify the identities of users, hosts, and clients, the directory can provide various authentication options:
Oracle Internet Directory can protect passwords by storing them as one-way hashed values. This approach secures passwords better than the approach of storing them as clear text or encrypted values, because a malicious user can neither read nor decrypt them if they are hashed.
During authentication to a directory server, a user enters a password in clear text. The directory server hashes this user password by using the specified hashing algorithm, then verifies it against the hashed password that has been stored. If the hashed password values match, then the server authenticates the user.
You can specify one of the following hashing schemes:
Authorization is the process of ensuring that a user reads or updates only the information for which that user has privileges. When directory operations are attempted within a directory session, the directory server ensures that the user has the requisite permissions to perform those operations. If the user does not have the requisite permissions, then the directory server disallows the operation. Through this mechanism, the directory server protects directory data from unauthorized operations by directory users.
The following features of directory access control can be used by applications running in the hosted environment.
In an enterprise or hosted environment, you can use the features of an LDAP-compliant directory to control access to application metadata--the information governing how applications behave and who can access them.
Because directory access control policies are stored as LDAP attributes, you can set metapolicies controlling who can modify them. This enables a global administrator to assign privileges to administrators of specific subtrees--for example, to administrators of applications in a hosted environment. Similarly, a global administrator can delegate to department administrators access to the metadata of applications in their departments. Department administrators can then control access to their department applications. In this way, you can implement access control on two levels: users and administrators.
This section includes:
In this case, the directory stores access control policies that external applications then read and enforce. When a user tries to perform an operation by using an application, the application verifies that the user has the correct authorization to perform the operation.
In this case, the directory serves as the trusted point of administration for all application-specific access control polices. To govern who can administer the access control policies of specific applications, you set access control policies at the directory level for these applications. Then, when a user attempts to change an application-specific access control policy, the directory verifies that the user has the correct authorization to make that change.
Figure 5-1 shows the relationship between directory access control and the application-specific access control mechanisms in a hosted environment.
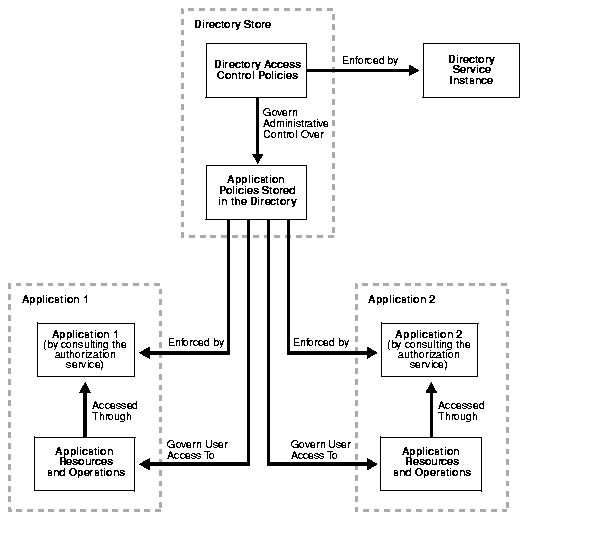
Figure 5-2 illustrates the various domains and the roles associated with them in the directory.
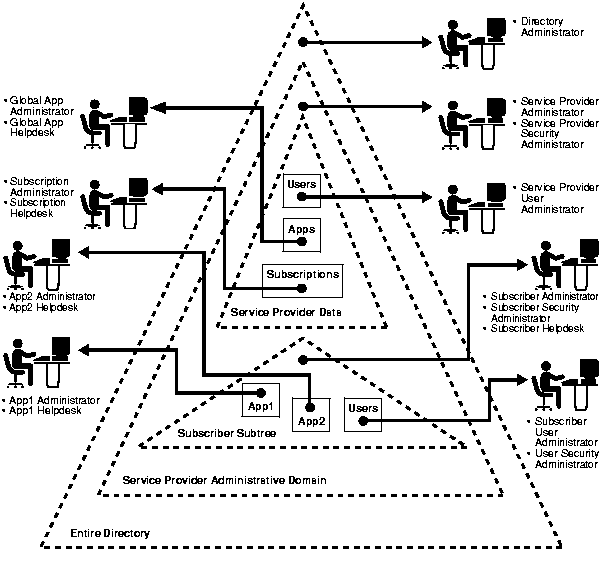
In Figure 5-2, each triangle represents a portion of a directory information tree (DIT).
Figure 5-2 shows only a single subscriber represented in the directory. In reality there are multiple subscribers, each with its own domain requiring protection from the others. Some of the protection domains in this model are:
Three types of role support the protection domains listed in the previous section. These roles enable the service provider or subscriber to customize access control if required.
|
 Copyright © 2001, 2002 Oracle Corporation. All Rights Reserved. |
|